The Ultimate Guide To Risk Management Enterprise
The Greatest Guide To Risk Management Enterprise
Table of ContentsOur Risk Management Enterprise PDFsRisk Management Enterprise Things To Know Before You BuyMore About Risk Management EnterpriseRisk Management Enterprise Fundamentals ExplainedRisk Management Enterprise for DummiesOur Risk Management Enterprise IdeasFascination About Risk Management EnterpriseThe 6-Second Trick For Risk Management EnterpriseThe Risk Management Enterprise StatementsSome Ideas on Risk Management Enterprise You Should Know
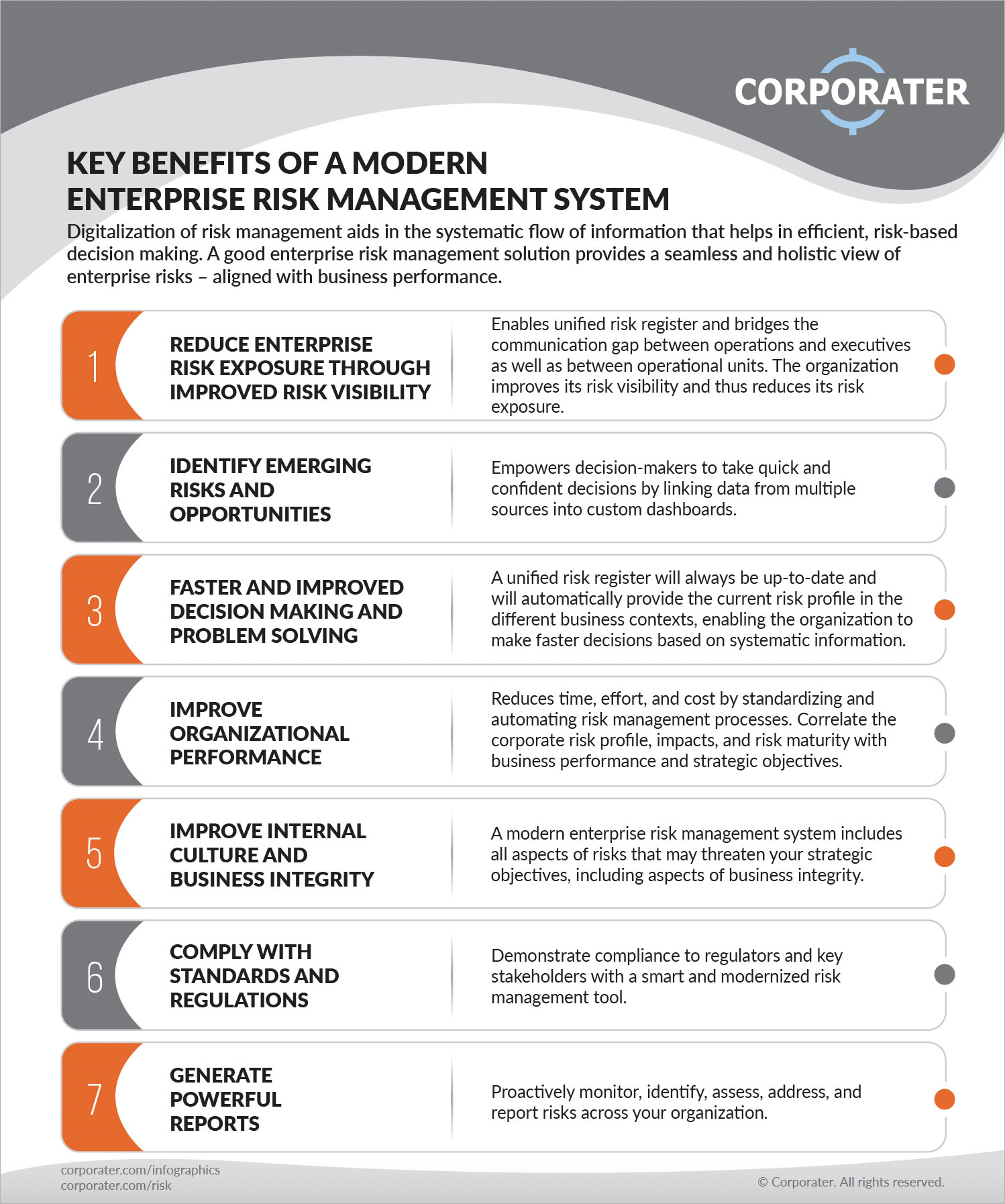
This system is conveniently accessible from any kind of edge and at any moment. That's why, accredited individuals can use its attributes to discover all the products and their threats. Therefore staff members remain knowledgeable about the dangers and recognize how to take care of such threats. For recognizing all the dangers within a company, Resolver Inc.This business threat monitoring software program aids centers manage workplace risks successfully. It automates operations, providing functions that benefit most organizations. Below are several of the vital attributes that make it an ideal threat administration software program. So, check them out. Unify your business functions and manage all sub-functions from a solitary danger knowledge system for a detailed understanding of your danger environment.
Not known Factual Statements About Risk Management Enterprise
The platform guarantees all divisions have access to the exact same info, fostering collaboration and avoiding miscommunication. The integrated system automates operations, making it less complicated to recognize, examine, and minimize dangers effectively across the company. Compliance, internal audit, and interior control teams can effortlessly access and examine comprehensive threat information, This feature gets rid of the requirement for hand-operated data transfers with smooth processes and software integrations that urge fostering.
The platform's intuitive user interface and cloud-based platform allow your organization to begin quickly. Get rid of the need for hand-operated duplicating of information in between systems. The instinctive interface makes certain that risk teams can quickly find out and use the new software program without training. It conserves time and reduces errors. It allows the sharing of information more understandably.
The control panel permits for fast and reliable sharing of risk condition and essential indicators, making certain everybody is well-informed. Customizable KRIs and KPIs enable tailored tracking of specific dangers and efficiency metrics.
Boosts responsiveness to arising hazards by offering real-time details. To take care of workplace risk efficiently Audit Board supplies AI-based remedies to bring even more effectiveness. This danger administration software program can be conveniently incorporated with other applications.
Not known Details About Risk Management Enterprise
Here are some of the essential functions of this software program that you have to be aware of. Gives clear presence right into how concerns impact one another, assisting to recognize the more comprehensive context and relationships in between risks.
Helps with quicker and more effective removal by highlighting the connections in between issues and their prospective options. Attach KRIs (Secret Risk Indicators) to various dangers and audit entities, permitting fast responses to altering service problems. This assimilation helps you stay active and proactive in danger monitoring. Problems it Fix: It makes it possible for fast reactions to altering organization problems, guaranteeing timely interventions.
It additionally aids take care of basic evaluations by ranking threats. Streamlines the process of planning, organizing, and performing threat assessments.
Rumored Buzz on Risk Management Enterprise
Simplifies the production and analysis of control examination plans, Supplies clear understandings into control analysis condition and results with interactive control panels. With One Count on, among the leading threat monitoring software, users can track their entire IT ecological community. It allows the measuring of threats and helps make educated decisions. Thus it boosts security and conformity.
It aids focus on achieving goals as opposed to browsing compliance barriers. Below are a few of its features that each center have to understand. So, have a look. NAVEX One's worker conformity services provide oversight and responses on training, code of conduct, and plans. Besides, it enables trusted whistleblowing and incident monitoring options that are certified and collaborative.
It promotes compliance, quality, and collaboration in coverage and resolution. It helps decision-making by offering clear and workable understandings acquired from comprehensive information analysis.
Control that can see or edit these aspects by setting details access civil liberties for individual customers, ensuring info security and tailored usability. Permits users to tailor their user interface by selecting and organizing essential information elements. Supplies a personalized experience by permitting customization of this where and exactly how information elements are displayed.
The Buzz on Risk Management Enterprise
It enables accessibility to real-time incorporated information instantaneously. This aids remove wasted time on hand-operated report compilation. Centers can make use of extensive information intelligence for quicker and a lot more enlightened decision-making. Furthermore, it permits the automatic development of stakeholder records for individuals or groups. Enables timely decision-making and lowers delays brought on by out-of-date information.
Diligent is a danger monitoring software application that permits optimizing performance, and enhances development. It likewise assists check dangers with ERM software application that includes integrated analytics and adapts to your company demands.
Streamlines the process of accumulating danger data from numerous components of the company. Offers management and the board with real-time risk understandings. Usage ACL's sophisticated analytics to spot threat patterns and anticipate dangers.
The 2-Minute Rule for Risk Management Enterprise
This allows companies to record risk understandings and red flags in the third-party vendor's safety and security record. This permits conserving threat evaluations as auditable files (Risk Management Enterprise). It likewise permits exporting them as PDFs. To finish the process companies can finish a reassessment date. Allows firms to catch and document danger insights and warnings in third-party supplier safety and security reports.
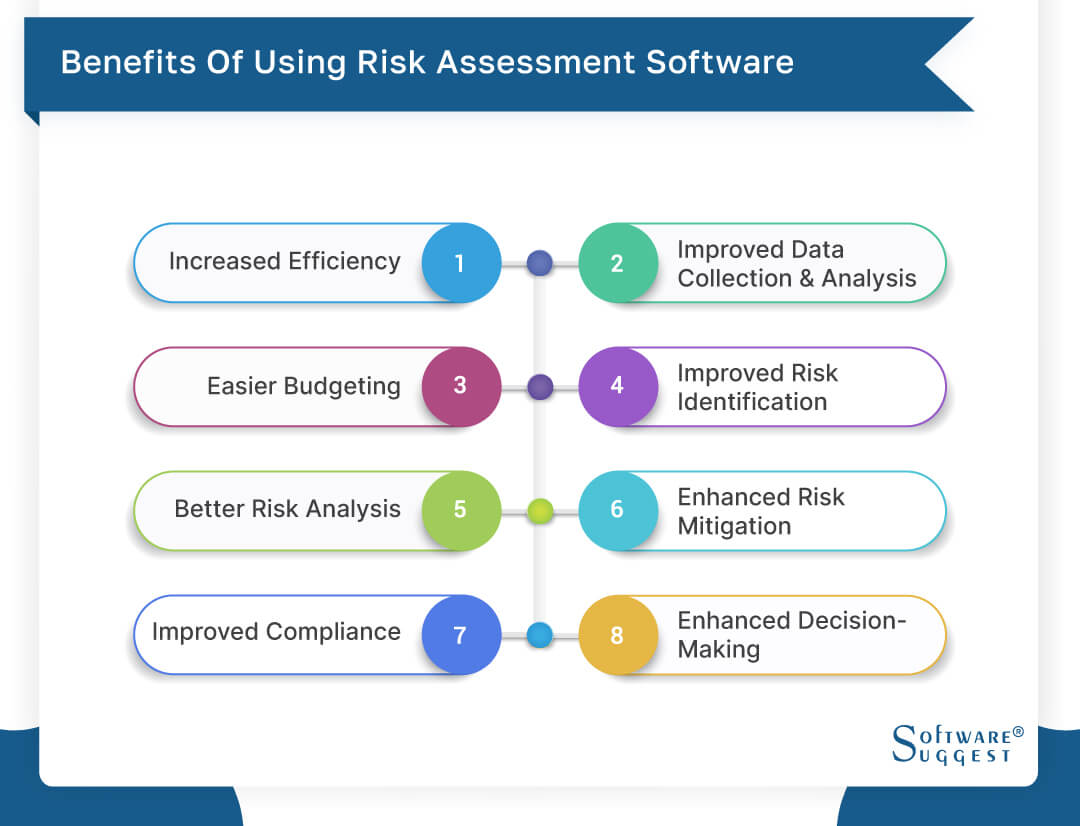
Recognizing threats beforehand aids a facility get ready for audits. It additionally minimizes risk via structured conformity and danger management. Because of this centers will not have to handle different systems for threat tracking. The users of Hyperproof can systematize danger administration in one area. It can aid accumulate and track all your dangers in the Hyperproof threat register.
With the assistance of these components, facilities can take care of, control, and address disturbances to shield your service proactively. This software program covers throughout your whole organization and likewise supplies a unified service for comprehensive risk administration tailored to your needs.
Risk Management Enterprise Things To Know Before You Get This
It enables smooth workflows and assimilations and lowers inefficiencies. It gives top-tier protection features to safeguard delicate information. This threat management software program is an excellent device for centers aiming to repair unneeded concerns or dangers. It comes with several sorts of attributes that make it details for ERM managers. Right here we have actually highlighted several of its crucial features for your advantage, so have a look.
Users can also utilize the AI-powered tools and pre-existing material to produce, evaluate, prioritize, and address threats efficiently. Enhances the process of configuring and inhabiting danger registers.
Control that can watch or edit these aspects by establishing certain gain access to rights for specific customers, ensuring information safety and tailored usability. Enables customers to tailor their user interface by picking and preparing necessary data elements. Gives a personalized experience by permitting personalization of where and exactly how data aspects are displayed.
It allows access to real-time incorporated data immediately. Facilities can use comprehensive data intelligence for quicker and more informed decision-making.
Some Known Incorrect Statements About Risk Management Enterprise
Diligent is a threat administration software that permits enhancing performance, and boosts growth. It also aids check risks with ERM software program that includes integrated analytics and adapts to your organization needs. This software includes numerous valuable features. Listed below we have actually highlighted the most vital ones. Check them out.
It also provides one-click records. It offers your management and board the real-time understandings they need. Streamlines the process of accumulating risk data from various components of the organization. It enables for simple personalization of reports and storyboards. Supplies leadership and the board with real-time risk understandings. Use ACL's sophisticated analytics to spot risk patterns and predict threats.
This permits business to record threat understandings and red flags in the third-party supplier's protection record. This permits conserving danger evaluations as get redirected here auditable papers. It likewise enables exporting them as PDFs. To complete the procedure business can finish a reassessment date. Makes it possible for business to record and record danger insights and warnings in third-party vendor protection records.
Determining threats ahead of time assists a facility plan for audits. It also decreases danger via structured conformity and threat management. Because of this facilities will not need to manage various systems for danger tracking. The customers of Hyperproof can centralize danger administration in one location. It can help gather and track all your dangers in the Hyperproof threat register.
The 3-Minute Rule for Risk Management Enterprise

With the aid of these modules, centers can take care of, control, and address interruptions to shield your business proactively. This software program extends across your whole company and additionally provides a unified remedy for comprehensive danger administration customized to your demands.
It makes it possible for smooth process and assimilations and lowers inadequacies. It provides top-tier protection functions to guard sensitive information. This danger administration software program is a perfect tool for facilities wanting to take care of unnecessary issues or risks. It features several kinds of features that make it certain for ERM managers. Right here we have actually highlighted a few of its essential attributes for your advantage, so have a look.
Some Ideas on Risk Management Enterprise You Need To Know
Users can additionally utilize the AI-powered devices and pre-existing web content to create, review, prioritize, and address threats efficiently. Improves the procedure of setting up and inhabiting threat registers.